Today we are thrilled to announce that the NKN Foundation Award 2024 goes to novon.tv, the new generation of decentralized live-streaming platform built on top of the largest DePIN communication platform NKN!
Since we published our NKN 2024-2028 roadmap, we received overwhelming interest in what are the immediate outcome of those major initiatives. Now we would like to give our community a 2024 mid-term upodate. For Q3 and Q4 in 2024, we are working towards the following deliverables:
The NKN network represents a leap forward in enabling decentralized AI inference, addressing the critical challenges of connectivity, permission, and privacy through its innovative peer-to-peer communication framework.
People often ask questions about what NKN can do outside NKN blockchain, for example:
Can we use NKN to enable real time communication between two Ethereum addresses?
Can we use NKN to do communication between different blockchain addresses, like Ethereum to Bitcoin?
Can we use NKN to communicate between web2 addresses (e.g. domain, email address) and web3 addresses (e.g Ethereum address, ENS)?
Now the answer is YES.
Built on top of the New Kind of Network (NKN) protocol, Universal Communication System (UCS) uses NKN as its network layer, effectively making NKN the TCP/IP layer in the UCS architecture. This groundbreaking system enables end-to-end encrypted communication without reliance on any centralized server, ensuring optimal privacy and security for all users.
Today we have officially integrated OpenAI chatGPT into nMobile secure private chat. Download nMobile today from Android/iOS app stores or APK and add chatGPT bot using the QR code. You can use it either in one-on-one private chat (recommended), or use at command @gpt in a group chat (both public group and private group). As […]
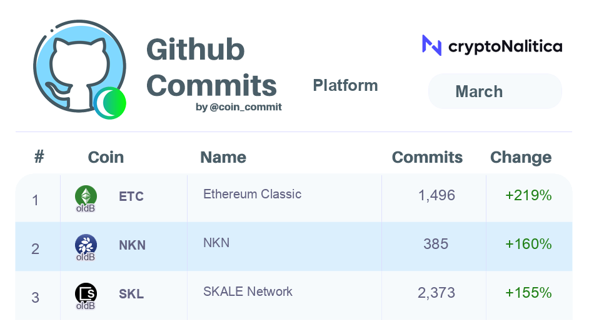
NKN developers have been busy, and here are the main achievements for first quarter of 2023.
We released a new mainnet version v2.2.0 at https://github.com/nknorg/nkn/releases. This version adds a few major features including client authorization, client message cache, transaction pool sync. In addition, this version contains several performance optimization, bug fixes and security patches. Upgrade is highly recommended.
Web 3.0 Pioneers – Future Storage Panel by experts from Filecoin, Bluzelle, ETHStorage and hosted by NKN.